Security Operating with Logic
Investigate how to use logic operators to make a security alarm using sensors
Questions to investigate
• How can logic operators be used with sensors to create a more complex conditional statement?
Prepare
• Ensure SPIKE Prime hubs are charged, especially if connecting through Bluetooth.
Engage
(Group Discussion, 10 minutes)
Engage students in a conversation about security.
Ask students to think about places that they keep secure (i.e. phones, computers, doors, etc.). Have students share how these areas are kept secure.
Launch a discussion about physical security options and ways to detect “break ins”. Prompt students to think about ideas like detecting movement or setting passwords.
Explore
(Small Groups, 45 minutes)
Students will investigate using two steps for more security.
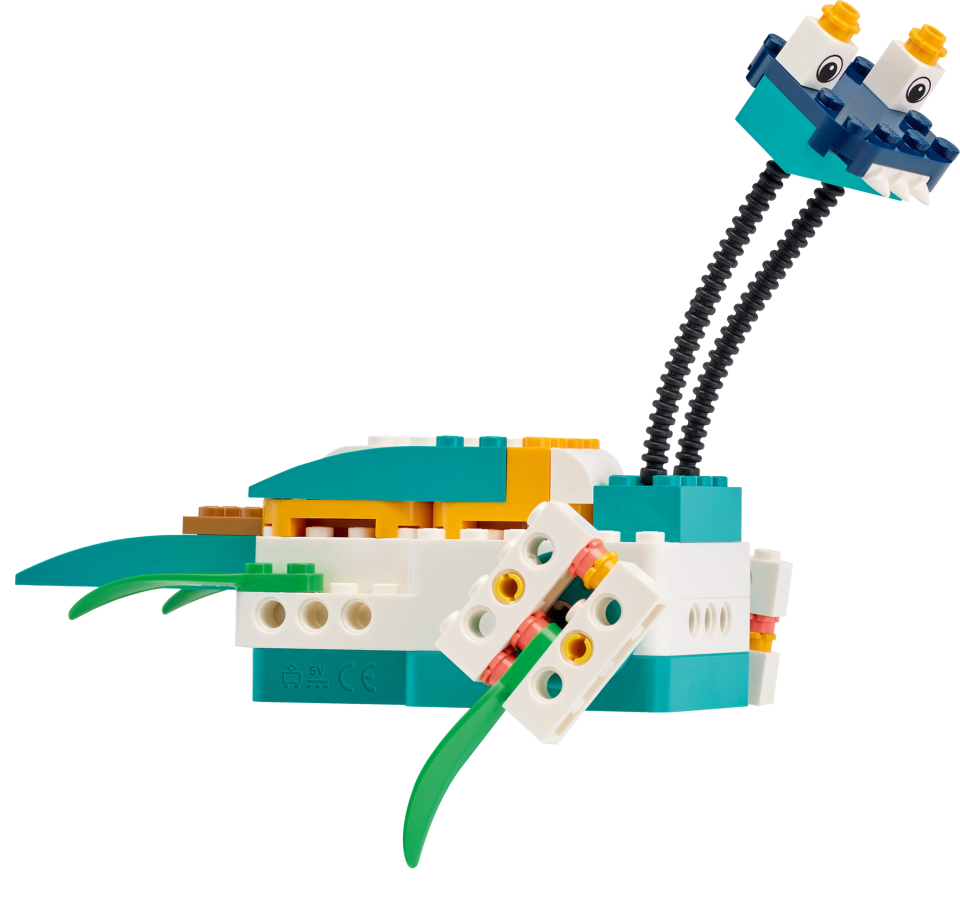
Direct students to the BUILD section in the SPIKE App. Here students can access the building instructions for the Quality Check Robot model. Ask students to build the model. The building instructions are also available at https://education.lego.com/en-us/support/spike-prime/building-instructions.
Direct students to open a new project in the Python programming canvas. Ask students to erase any code that is already in the programming area. Students should connect their hub.
Ask students to create a security device that alerts your movement and then requires a color-coded password. Discuss the two sensors included in the model and how these might be used to create a physical alert device.
Ask students to write a pseudocode program that explains how their program should work. The program should include:
• using the distance sensor first to detect motion
• then using the color sensor as a pass code
• and include at least one logic operator
Ask students to use their pseudocode to create their program. Remind students to use code comments in their program to indicate the expected actions.
Allow students time to test and modify their program as needed. Remind students to watch the console for error messages.
Explain
(Whole Group, 10 minutes)
Discuss various program examples together as a class to find what is effective. Ask students questions like:
• How can sensors be used to create a security device?
• How did the logic operator work in your program?
• How can you create two step security in your device?
Elaborate
(Small Groups, 25 minutes)
Challenge students to use a different logic operator in their security device.
Ask students to write a new pseudocode to change the way the program will work by using a different logic operator. Students can choose to add a second logic operator to their program or replace the one in their current program.
Allow students time to modify their program according to the new pseudocode. Students should test and refine their program. Remind students to watch the console for error messages while testing their program.
Evaluate
(Group Exercise, 15 minutes)
Teacher Observation:
Discuss the program with students.
Ask students questions like:
• What happened when you changed the logic operator?
• When adding more than one logic operator, what are potential bugs to consider?
• How were the sensors used to create security? What are other ways you could use sensors in your programs (other sensors to use)?
Self-Assessment:
Have students answer the following in their journals:
• What did you learn today about using multiple steps of security?
• What characteristics of a good teammate did I display today?
• Ask students to rate themselves on a scale of 1-3, on their time management today.
• Ask students to rate themselves on a scale of 1-3, on their materials (parts) management today.
Teacher Support
Students will:
• Investigate using sensors for security
• Create two-step security programs
• SPIKE Prime sets ready for student use
• Devices with the SPIKE App installed
• Student journals
CSTA
2-CS-02 Design projects that combine hardware and software components to collect and exchange data.
2-AP-10 Use flowcharts and/or pseudocode to address complex problems as algorithms
2-AP-13 Decompose problems and subproblems into parts to facilitate the design, implementation, and review of programs.
2-AP-16 Incorporate existing code, media, and libraries into original programs, and give attribution.
2-AP-17 Systematically test and refine programs using a range of test cases.
2-AP-19 Document programs in order to make them easier to follow, test, and debug.